
Description This article describes techniques on how to identify, debug and troubleshoot issues...
The community is a place to collaborate, share insights and experiences, and get answers to questions.
Search here or look around to get started.
Become a member today to get answers to questions, collaborate, share insights and experiences.

Welcome to your new Fortinet Community!
You'll find your previous forum posts under "Forums"

Description This article describes techniques on how to identify, debug and troubleshoot issues...
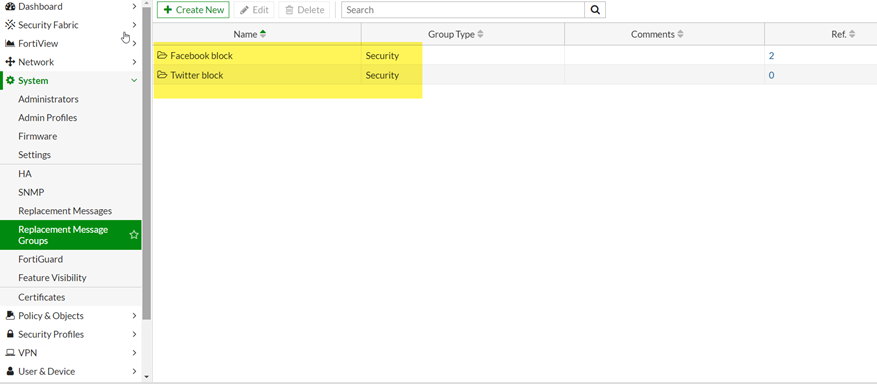
Description This article describes how to customize replacement messages for individual web filter...

Description This article explains how to reset a FortiGate to factory defaults. Scope This command...
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.